Sometimes, a device does not respond as intended. This could be due to a firmware problem, incorrect protocol implementation on the device, wrong IOC configuration, inaccurate metadata, or everything in between. In such cases, it’s quite handy to know what exactly is being sent to the device to determine which side is wrong.
The easiest way to check this is by using the IOC asynReport facility and enabling logging to monitor the data being sent. But what if, for some reason, we don’t want to modify the IOC? Or we don’t have the IOC yet and struggle to get the “manual” communication working?
One idea is to use Wireshark, but I’d like to share a different one today. I’d like to show how to intercept communication from point A (our terminal, probably running telnet) to point B (our device) and log what is sent across.
The tool I will use to create a man-in-the-middle situation is the Multipurpose relay (SOcket CAT), or socat for short.

A one-liner that does the job looks like the following:
socat <flags> TCP-LISTEN:<local-listen-port>,fork,reuseaddr TCP:<device IP:port>
For example,
socat -v -x TCP-LISTEN:4321,fork,reuseaddr TCP:192.168.1.10:123
Where:
vis to set up verbose text dumpxto dump in hexadecimal,fork,reuseaddrallows address reuse, and forks a new process for each connection
Then connect to the port issued by socat from another console and try to exchange data with the device. If everything goes well, you should see something similar to the socat output below:
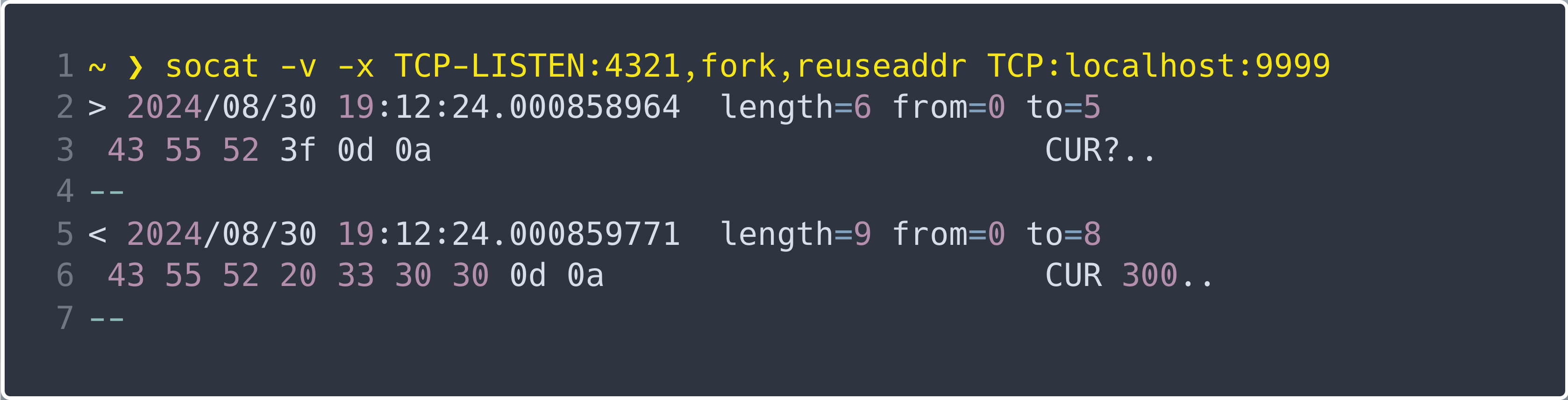
Lines 2 and 3 show that I sentCUR? to the device, and lines 5 and 6 show the answerCUR 300received from the device. My example points to localhost for local port and for the device, because I simulate a simple device to demonstrate the setup.
I hope this tip enhances your troubleshooting toolkit 🚀